Security Breach at Adobe for 2.9 MILLION Customers
See prior blog posts on Adobe Creative Cloud.
Adobe Systems has announced a major security breach of it systems. Customer data was compromised, and source code also.
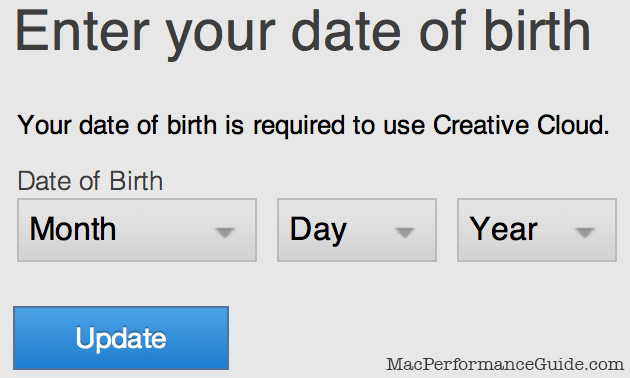
UPDATE Oct 29, 2013: the security breach was MASSIVE, affecting 38 million customers. You might fairly ask why Adobe would ask for date of birth as a requirement for Adobe Cloud, a point I commented on months before this security breach, noting “patently offensive... and why promote identity theft?”. But that ought to be obvious—just not to Adobe.
The source code breach is more subtle and pernicious; it could allow (for example), a hacker to build a perfect copy but with a Trojan Horse back door built-in and copy protection removed. Never download “free” software that you know is not free.
Isn’t it upsetting that Adobe asks for your date of birth? Which is very helpful for identity theft. Was the date of birth encrypted or was it compromised in full?
It’s hardly an Adobe specific issue, as I discuss in So You Actually Trust Your Sensitive Data to Apple’s iCloud ?.
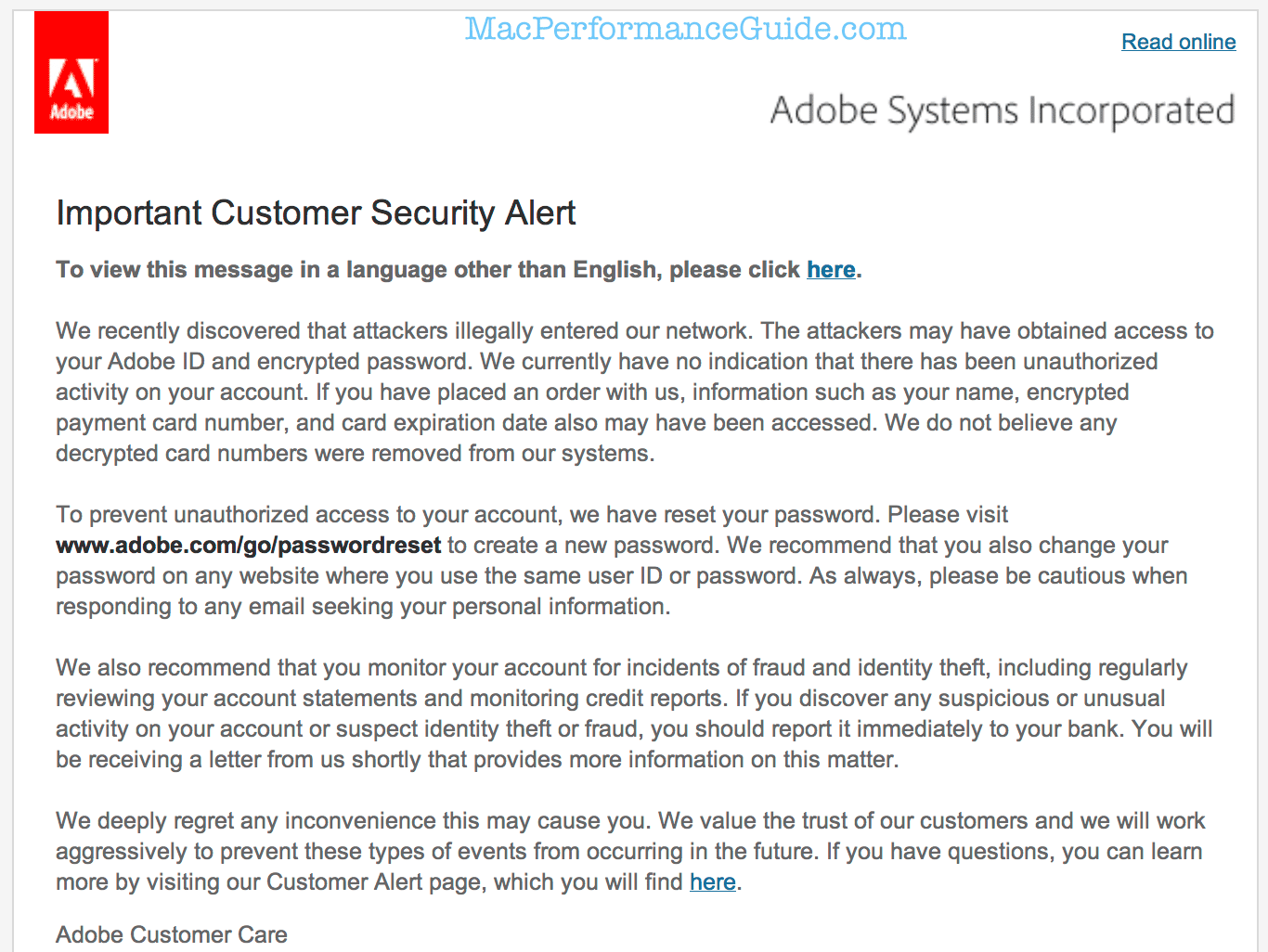
Cyber attacks are one of the unfortunate realities of doing business today. Given the profile and widespread use of many of our products, Adobe has attracted increasing attention from cyber attackers. Very recently, Adobe’s security team discovered sophisticated attacks on our network, involving the illegal access of customer information as well as source code for numerous Adobe products. We believe these attacks may be related.
Our investigation currently indicates that the attackers accessed Adobe customer IDs and encrypted passwords on our systems. We also believe the attackers removed from our systems certain information relating to 2.9 million Adobe customers, including customer names, encrypted credit or debit card numbers, expiration dates, and other information relating to customer orders. At this time, we do not believe the attackers removed decrypted credit or debit card numbers from our systems. We deeply regret that this incident occurred. We’re working diligently internally, as well as with external partners and law enforcement, to address the incident. We’re taking the following steps:
- As a precaution, we are resetting relevant customer passwords to help prevent unauthorized access to Adobe ID accounts. If your user ID and password were involved, you will receive an email notification from us with information on how to change your password. We also recommend that you change your passwords on any website where you may have used the same user ID and password.
- We are in the process of notifying customers whose credit or debit card information we believe to be involved in the incident. If your information was involved, you will receive a notification letter from us with additional information on steps you can take to help protect yourself against potential misuse of personal information about you. Adobe is also offering customers, whose credit or debit card information was involved, the option of enrolling in a one-year complimentary credit monitoring membership where available.
- We have notified the banks processing customer payments for Adobe, so that they can work with the payment card companies and card-issuing banks to help protect customers’ accounts.
- We have contacted federal law enforcement and are assisting in their investigation.
MPG: Joy. So to protect myself I can sign up for a service which also will want some sensitive information and probably auto-bill me next year.
If I were a hacker, an email that looks like this would be a juicy thing to send a few million of right about now, containing a fake URL to click on: never, NEVER click on links found in an email. That password link has to be typed in by hand (good), but the “please click here” thing is not a good idea.

 diglloydTools™
diglloydTools™