The Most Serious Apple Software Quality Failure Yet: Logging-in 'root' without any password
Update 29 Nov: Apple has issued a patch for this bug (gotta give 'em credit for acting fast, but a bug of this massive severity should NEVER ship and speaks to very poor quality control practices). More info in About the security content of Security Update 2017-001.
Update 30 Nov: Apple issues a fix for the fix. Cute—Apple botches the first fix and has to issue a 2nd fix the next day. Speaks volumes. Note the lack of a version number for the fix—why? This generates even more doubt as to whether the fix fixes it.
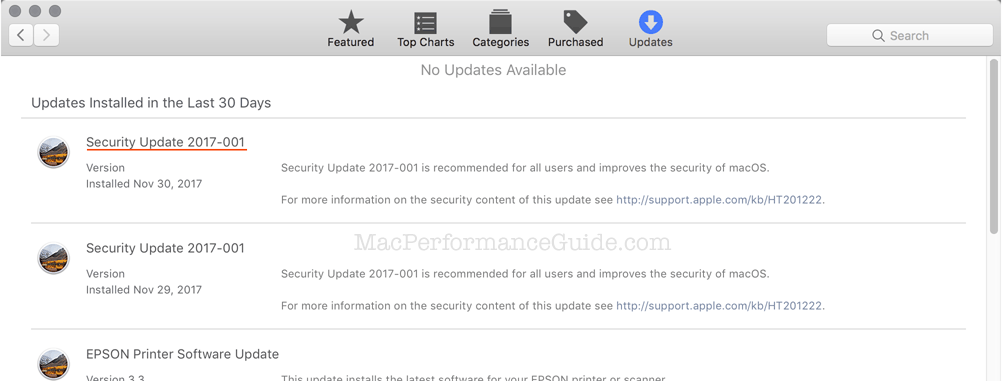
It is critical to install the patch RIGHT NOW. To do so, open App Store and click on Updates. If the security patch has been installed, you’ll something like this, below. If not, click Update to install the patch.
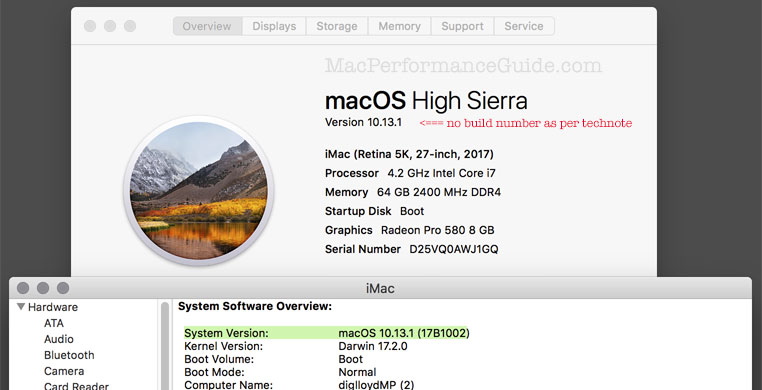
Disturbing: after the update, About this Mac does not display the new build number in About this Mac as per the technote. Another bug it seems, but as I see it: more sloppy work.
I also found that on my father’s Mac, even though “Install System Data Files and Security Updates” was enabled in App Store Preferences, the patch had NOT been installed—incredibly, yet another bug. A comedy of errors that ought to be intensely embarrasing to Apple.
Security Update 2017-001
Released November 29, 2017
Directory Utility
Available for: macOS High Sierra 10.13.1
Not impacted: macOS Sierra 10.12.6 and earlier
Impact: An attacker may be able to bypass administrator authentication without supplying the administrator’s password Description: A logic error existed in the validation of credentials. This was addressed with improved credential validation.CVE-2017-13872
When you install Security Update 2017-001 on your Mac, the build number of macOS will be 17B1002. Learn how to find the macOS version and build number on your Mac.
If you require the root user account on your Mac, you will need to re-enable the root user and change the root user's password after this update.
Original post...
Apple Core Rot is alive and well. MPG reiterates its advice to hold off at least 6 months before installing High Sierra. See also How to Disable Downloading of macOS High Sierra.
For a temporary fix/workaround until Apple issues a patch, see How to enable the root user on your Mac or change your root password.
I blame incompetence high up the management chain: undisciplined, no planning, arbitrary changes and generally poor judgment on everything that has appeared in the past 4-5 years. All on a calendar scheduled with a damn-the-quality-ship-it-now attitude.
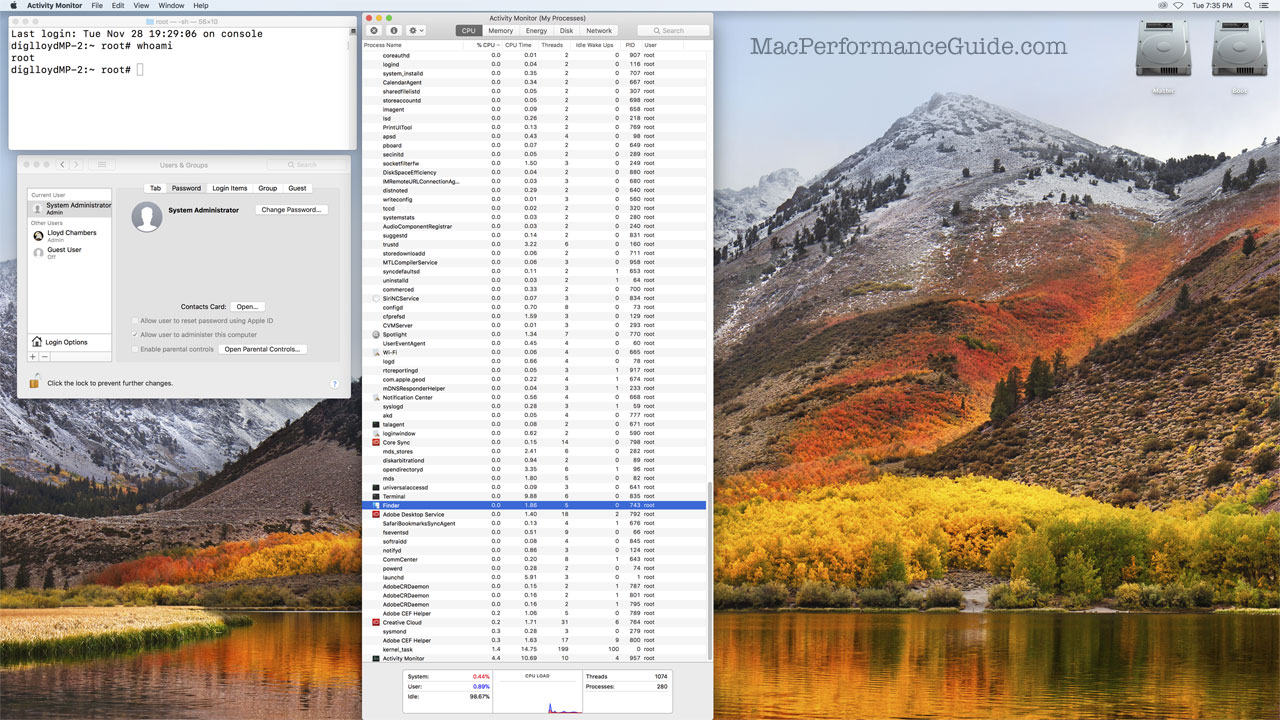
I was able to reproduce the root login with no password in System Preferences as well as at the startup login prompt. macOS even nicely set up an all new user desktop for 'root' for me. User 'root' has unfettered access to everything, as show in in the image below with all processes in Activity Monitor.
Rather than repeat a well-written article I refer readers to ArsTechnica: macOS bug lets you log in as admin with no password required.
In one of Apple's biggest security blunders in years, a bug in macOS High Sierra allows untrusted users to gain unfettered administrative control without any password.
The bypass works by putting the word "root" (without the quotes) in the user name field of a login window, moving the cursor into the password field, and then hitting enter button with the password field empty. With that—after a few tries in some cases—the latest version of Apple's operating system logs the user in with root privileges. Ars reporters were able to replicate the behavior multiple times on three Macs. The flaw isn't present on previous macOS versions.
This is not a “blunder”: it is the direct result of longstanding issues in software development—issues like this being inevitable in my view. Note also that the Disk Utility password exposure bug makes this NOT a one-off issue. Not to mention breaking sudo.
Why the hell don’t high level heads roll when something like this happens? It is not excusable in any way shape or form.
The downside for users is potentially horrific: loss of all bank accounts (think keyboard sniffer malware), impersonation, downloading child porn and then calling the cops, whatever—someone’s life could be ruined in many ways, financially, criminally and so on.
Apple’s software quality is manure-grade these days and this latest fiasco calls for Tim Cook to either step down as having failed in the most fundamental way, or direct a few billion at fixing the software incompetence he seems intent on never fixing. All that self-serving drool about respecting user privacy amounts to a city-size pile of compost in this context. Start by letting heads roll, with Craig Federighi being a good start.
Below, logged in as root, every process and application has unfettered root access to macOS.
Kevin B writes:
I agree with you about the fact that someone very high up in management at Apple needs to lose their job over the High Sierra root bug … but why Tim Cook or Eddie Cue?
Not that they don’t have their faults, but Tim’s no techie and Eddie Cue has nothing to do with this issue. To me the person who needs to go is Craig Federighi. He is the one in charge of software development at Apple. I’ve never understood why so many people seem to have a man crush on Craig … the decline in software quality at Apple that you (rightly) complain about began when Bertrand Serlet left and Craig took over. It’s time to ignore the fact that he is a good presenter and does have great hair and judge him on the quality of the work the people he supervises produces … which would result in his dismissal.
MPG: my mistake, yes it’s Craig Federighi at issue methinks (corrected above).
In my book the buck stops with the CEO (Tim Cook) and so I hold him accountable . He is the one to right the ship and if he does not, then he bears the failure first and foremost, not his underlings. The Apple ship has been listing for at least 5 years; I first started the Apple Core Rot section back in February of 2013.
Top level executive are paid dumptruck-full piles of $100 bills and ought to be held to standards far higher than rank and file employees as to performance. But Tim Cook keeps bringing in world’s-best profits, which is what makes ignoble software quality ignorable.

 diglloydTools™
diglloydTools™